Information gathering is the 2nd phase of the Kali Linux Methodology. In this phase, we collect as much information about our target, such as Domain Name Server (DNS) hostnames, IP address, technologies used, etc. I will deliberate some tools available to collect information of the target.
Public Resources
There are some sources or tool on the internet where you can gather information regarding target domain and it’s open to the public. Here are some of them:
Alexa.com
Contains the database information about the websites.
Archive.org
Contains an archive of a website. You can see the previous website before it gets updated. You might find some vulnerabilities on the old machine. Some admins would likely just kept them.
Robtex.com
For domain and network information
Whois
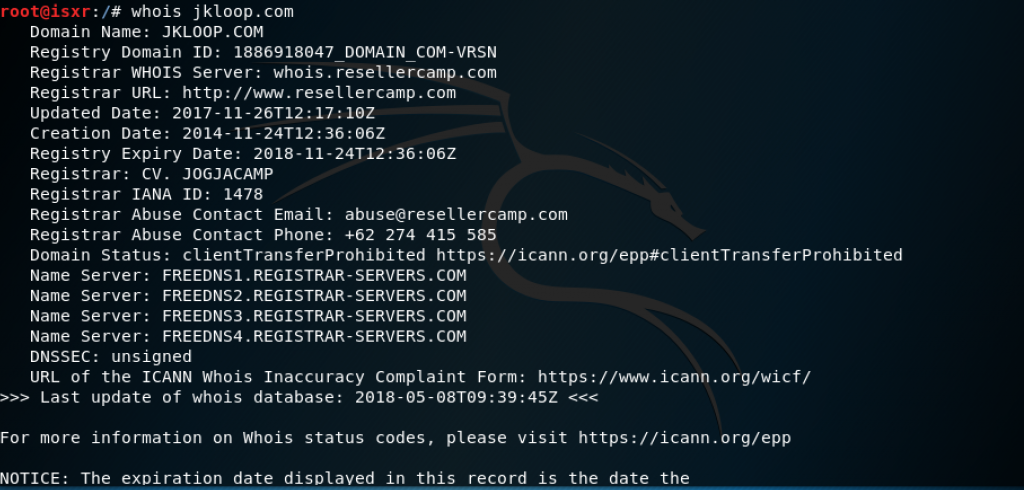
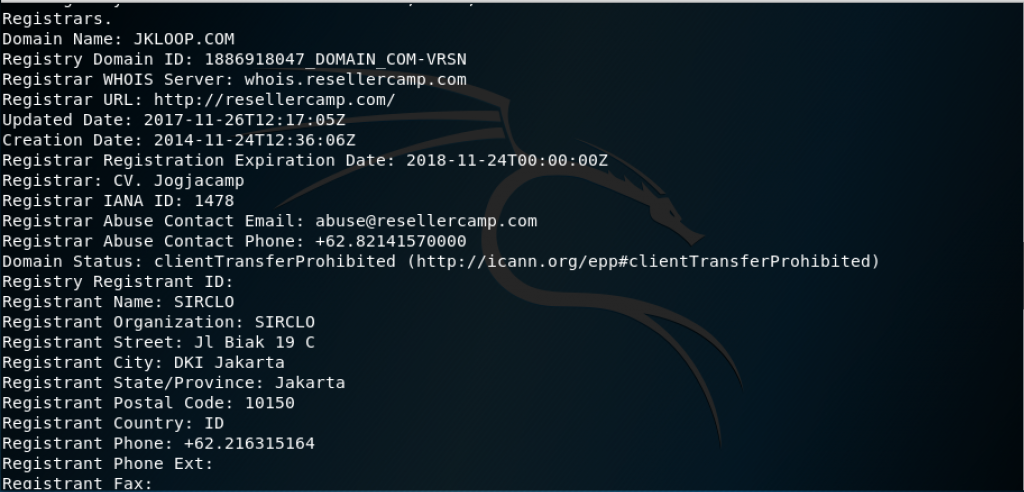
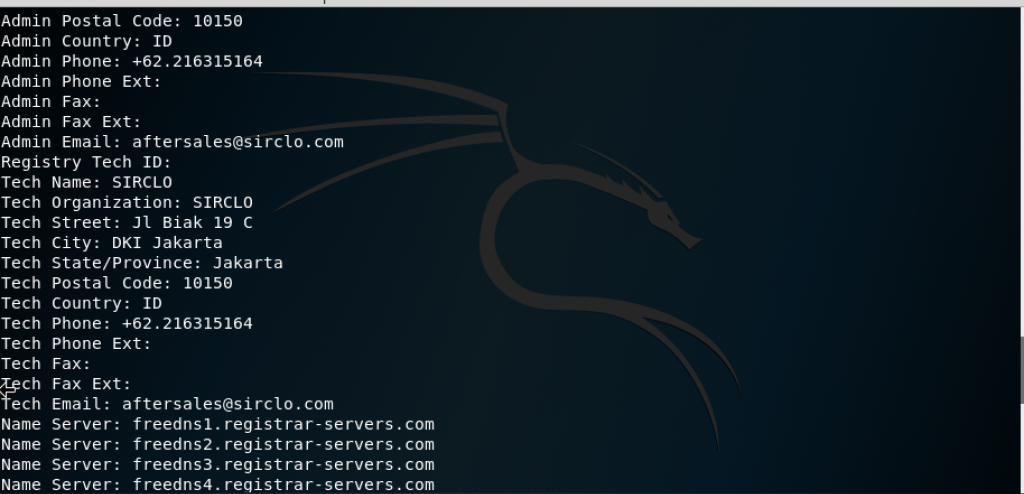
From the whois command, we get the DNS server and the contact person of the domain which will be very useful later. Other than using a command line, whois can be used through website www.whois.net.
Analyzing DNS records
Find IP address using the host command
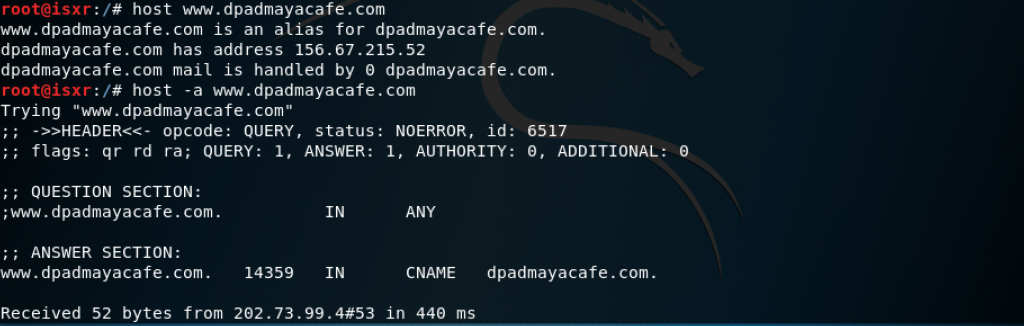
As you can see, www.dpadmayacafe.com IP address is 156.67.215.52
You can add -a to query any records.
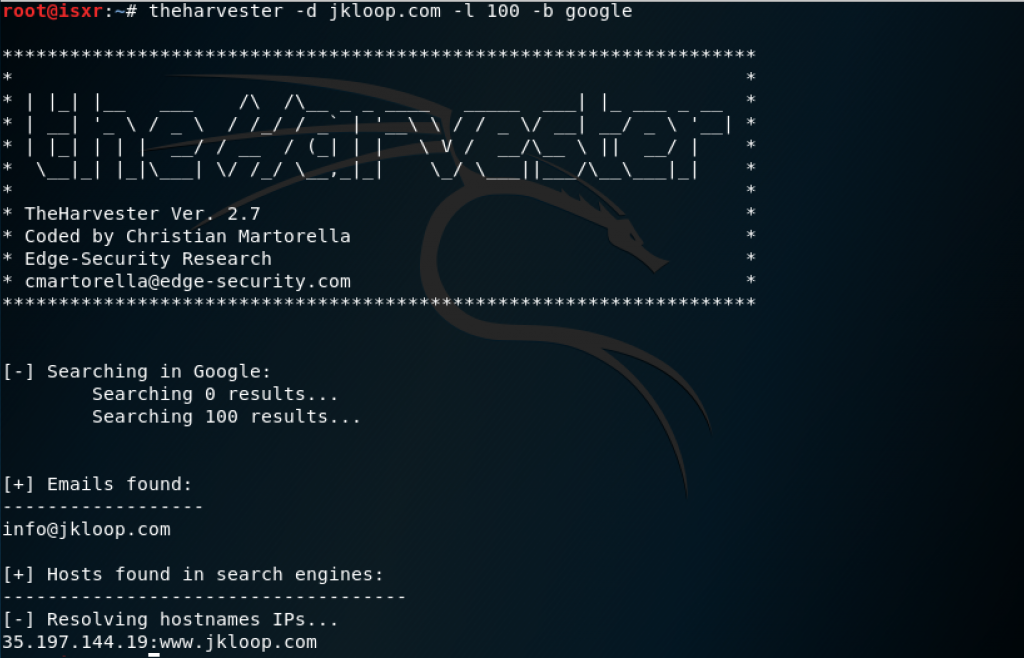
theharvester
is an email account, username, and hostname gathering tool
If we want to search email accounts and hostnames from a target domain, with maximum 100 results and using google:
theharvester -d domain.com -l 100 -b google